Are your computer and online accounts secure? Are you sure? Because cybercrime is rampant! The days of gun-waving bank robbers are mostly over. Your ex-boy or girlfriend is not likely to break into your apartment to snoop. Unfortunately, if your computer is not secure, your bank account and social life can be stolen by cybercrime. Even if you are not tech-savvy, it is critical to secure your computer, smartphone, and online accounts. I can help you do just that. I promise to make this computer security guide a clear, easy to follow step-by-step process.
I am not tech savvy. How can I make my computer and online accounts secure?
Even if you are a novice, you can secure your computer and online accounts by taking the following steps:
- Make sure your PC is clean by running a quick malware scan
- Use a start-up scan to disable all unnecessary programs
- Clear your browser’s history
- Install a simple key scrambler program on your PC
- Bookmark all your essential social and financial websites
- Use a password manager to generate unique random passwords
- Keep your master password in a paper notebook!
- Install a full security suite program to monitor your computer and smartphone for spyware, viruses, and unauthorized webcam and microphone access.
- Download and install a two-factor authentication (2FA) app on your smartphone.
- Activate 2FA security login for your online accounts.
- When outside your home, use a VPN connection
- Use common sense online and in real life!
This process is most straightforward on a personal computer. I will walk you through each step above, and I will make sure things are clear using pictures and detailed instructions. By the end of our trip together, you too will be a virtual SecureHomeHero! And one more thing, I will do my best to use free programs or very reasonably priced ones.
Step 1, How to remove harmful malware from your PC
There are many programs that spy on you and damage your computer; they are called malware. Some malware belongs to corporations collecting marketing data, and some malware is more malicious.
We need to start with a clean slate, so let’s install a simple program that scans your computer against malware and removes harmful programs.
MalwareBytes is a great one. It is free to use, and you get a 14-day free access to MalwareBytes premium (more on that later.)
Click on this link to download MalwareBytes, choose the “free download” on the top right of the screen, and then I will walk you through installing and using it.
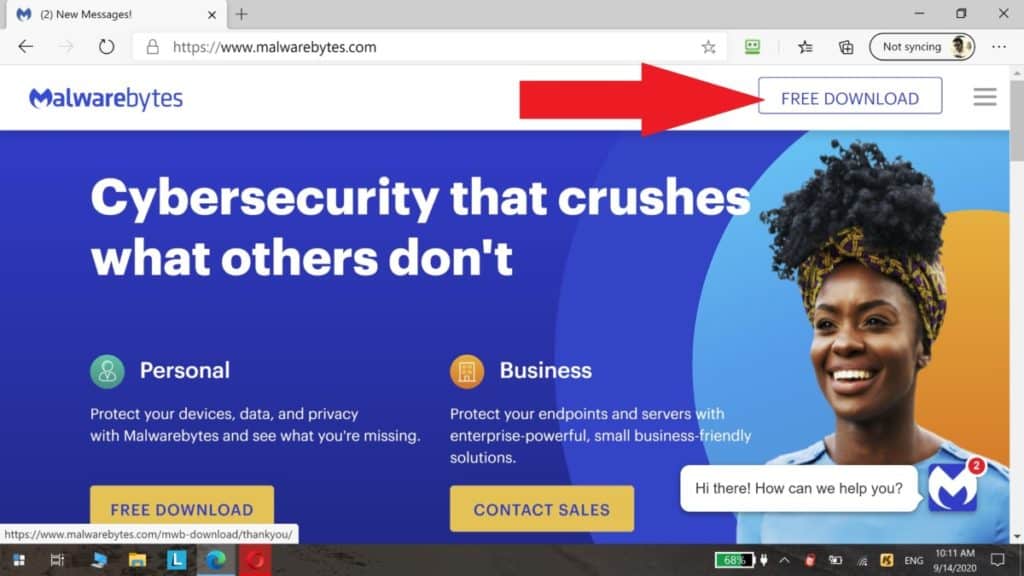
The downloaded file will most likely appear on the bottom of your internet browser (otherwise, look for the “MBSetup.exe” file in the “downloads” folder on your computer.)
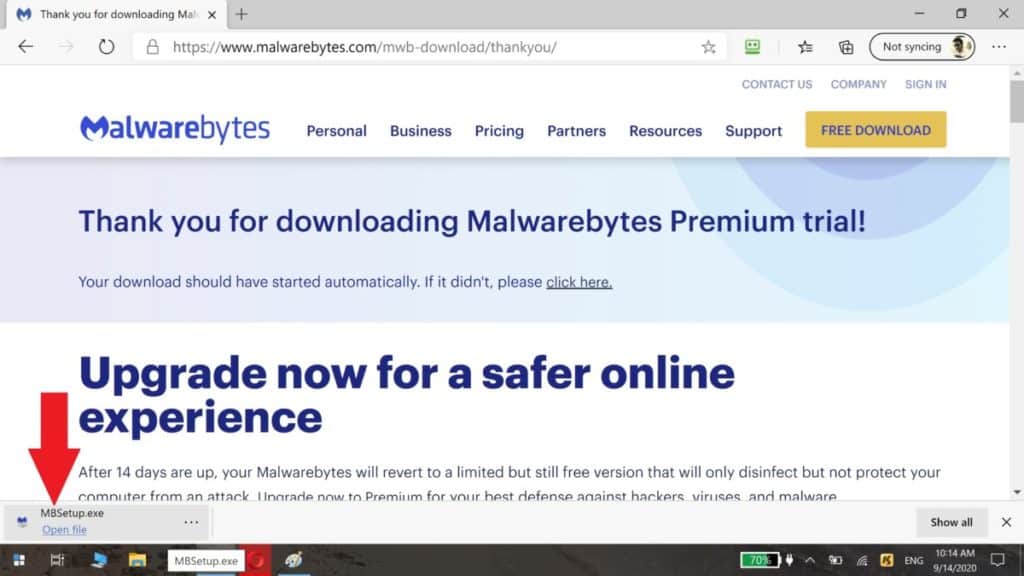
Click the “MBSetup.exe” file and follow the on screen installation instructions. Once the installation is complete, your MalwareBytes program will start.
Next, click the scan button.
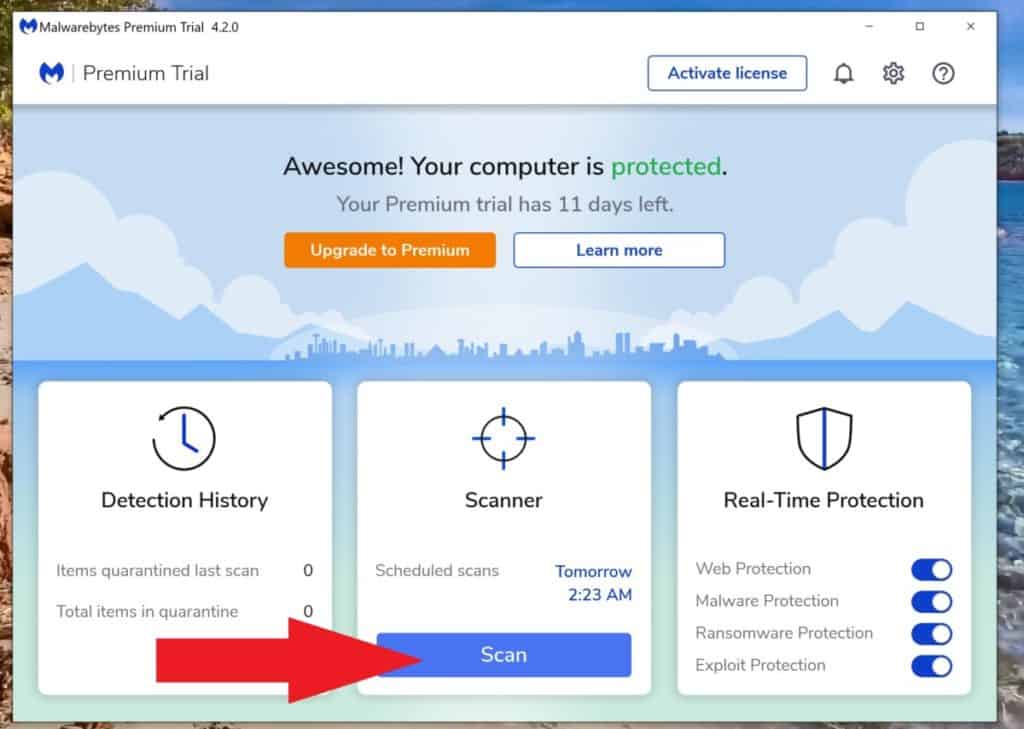
The scan may take a few minutes. Once completed, if you have suspicious files on your PC, MalwareBytes may suggest specific actions. Please follow the recommended actions to insure these file are removed.
Congratulations, you finished the first step towards becoming a digital SecureHomeHero!
Step 2, How to quickly disable unnecessary bloatware programs from your PC
When you buy a new computer, the manufacturer (such as Dell, HP, Lenovo..etc) often loads it with unnecessary and annoying programs. These programs (called bloatware) slow down your computer and bother you with notifications.
We need to unburden your computer, so let’s find the programs that automatically load every time you start your computer, then you can choose the ones to disable. This is an easy process:
- On your Windows PC, simultaneously press the ctrl+Shift+Esc keys.
- The “Task Manager” will open.
- Click on the “Startup” tab on top.
- You can now see a list of the names, company, and status of all programs that automatically load when your computer starts.
- Go through the list, one by one, and decide which programs you do not need. Then right-click on the word “enabled” and choose “disable” from the list.
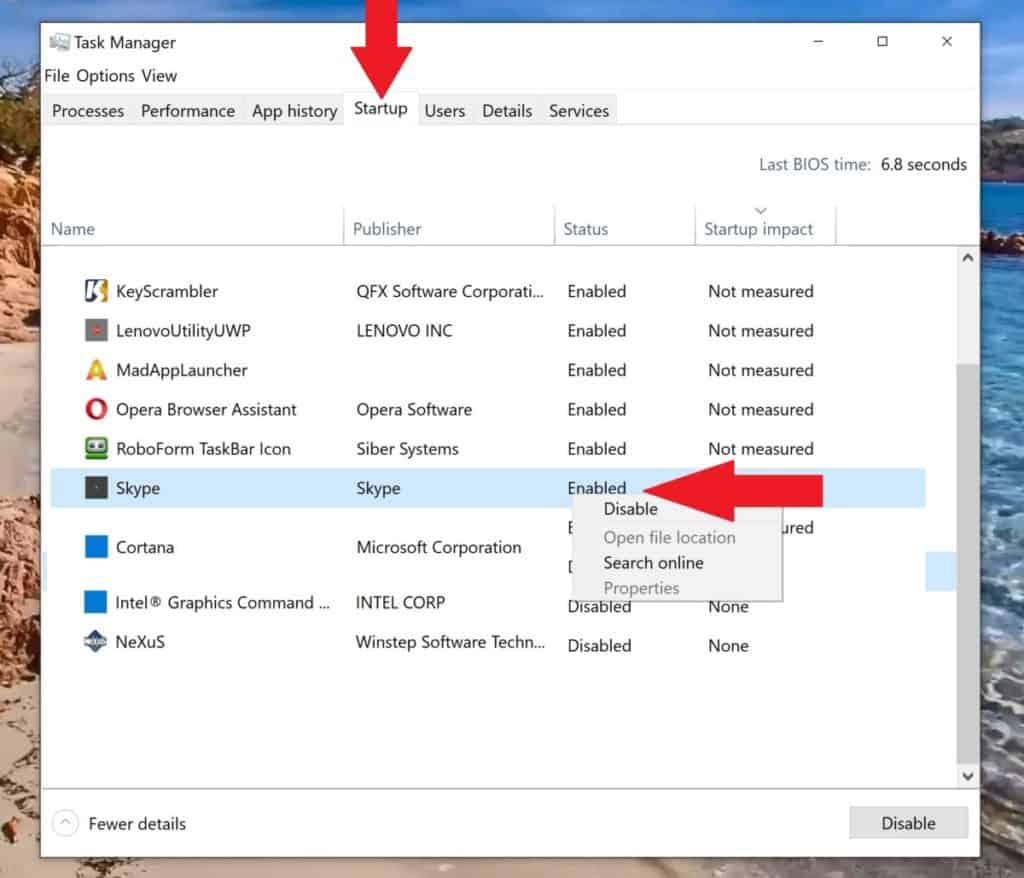
For example, I do not use Skype, so I do not want it constantly running in the background; I chose to disable it.
What if you mess up? Do not worry; you can always come back and re-enable a program.
6. Now, restart your computer and then come back to this SecureHomeHero.com page!
Step 3, How to clean your browser’s history
Welcome back. Your computer is clean! Well, almost.
Internet browsers keep a log history of all the internet pages you visited, and these websites also keep trackers (called cookies) on your computer. Cookies are how Amazon tracks your shopping habits and how Yahoo gives you only the news that interests you. Cookies also keep you logged into your email accounts, even after you close the browser.
Let’s clear your browsing history. This will achieve two things:
- First, it will remove all the cookie trackers from your computer, and
- Second, it will log you out of all email, social, and other online accounts.
The instructions on how to clear your browsing history are pretty similar across browsers (such as Microsoft Edge, Google Chrome, Firefox…etc.).
- Open your browser
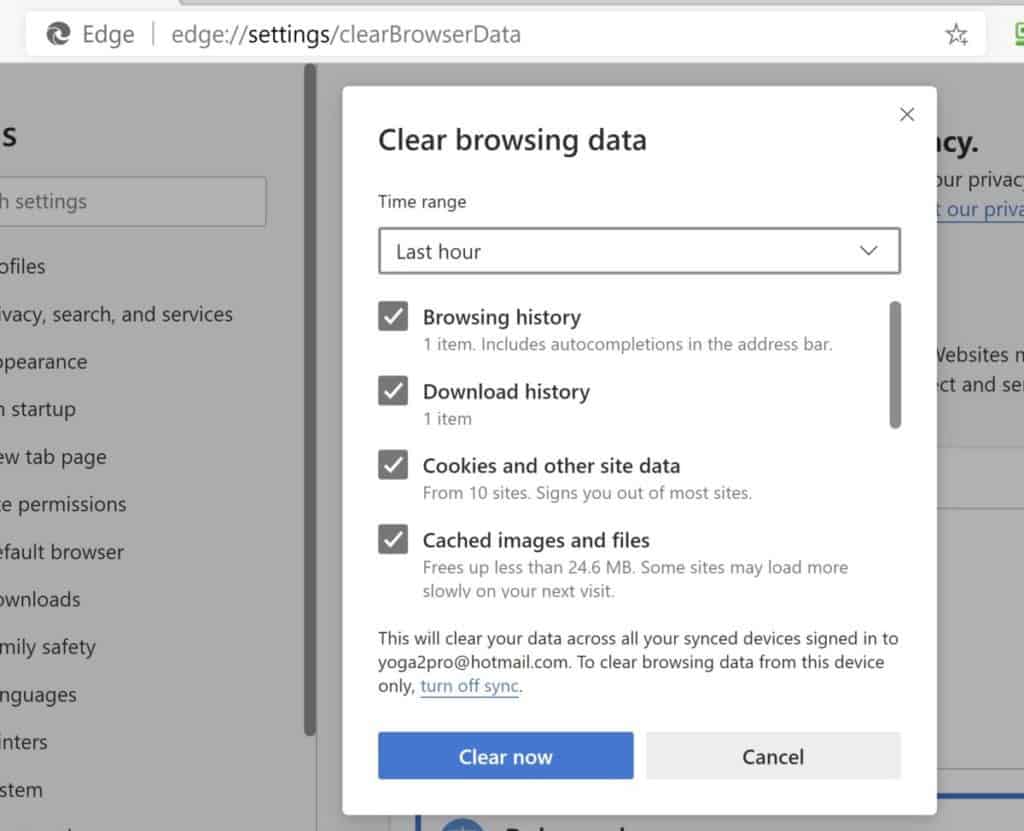
- Simultaneously press the ctrl+Shift+del keys
- A small “clear browsing data” window will open
- From the drop menu, choose “All time.”
- Click “Clear Now”
If the instructions above did not work for your particular browser, do a quick google search.
Step 4, Install a simple anti-keylogger program
One of the most evil ways people can steal your identity, passwords, and take over your digital life is through key loggers.
What is a key logger?
Keyloggers are hidden malicious software that record every keystroke you make on your keyboard, then send the information to a third party (the hacker.) Now the hacker knows the sites you visit, your usernames, passwords, and every word you typed on your PC.
How can I protect my computer against keyloggers?
First, install an anti-malware program (such as MalwareBytes from step 1), scan your computer, and remove all malicious programs. Second, install a key scrambler program (such as KeyScarmbler) to guard you against future attacks.
Since you already used MalwareBytes in step 1 to remove malicious software, let’s install a simple free program that protects you from keylogging software.
KeyScrambler is a great one. The free version will work with your web-browser, which is the most vulnerable program. If you would like to protect many additional programs, such as word processors, choose the premium version.
Here is a link to download KeyScrambler.
- Look for the “KeyScrambler_Setup.exe” file at the bottom of your browser, or in your “downloads” folder
- Click the “KeyScrambler_Setup.exe” file and follow the on-screen installation instructions.
- At the end of the installation, you will have to restart your computer. Make sure to come back to this SecureHomeHero.com page so we can continue our digital journey.
After the installation is complete, start the KeyScrambler program and let’s customize it together:
- Look in the bottom right corner of your screen for the icon with the KS symbol (color may differ)
- Right-click the icon
- Choose “options”
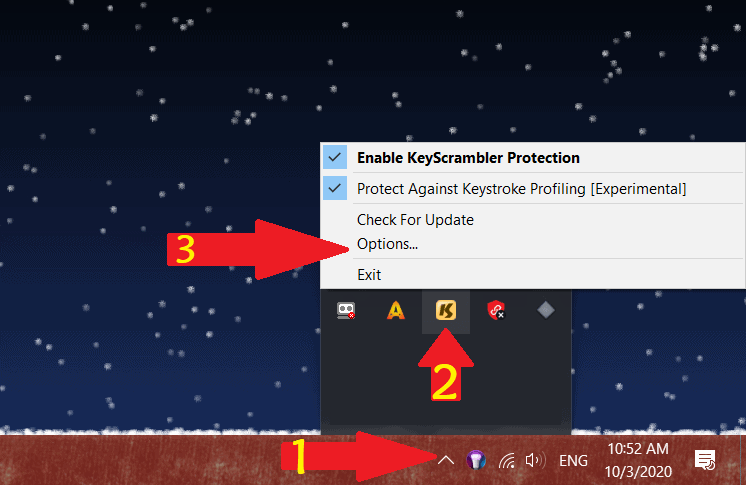
4. Make sure the “start KeyScrambler when windows starts” box is checked
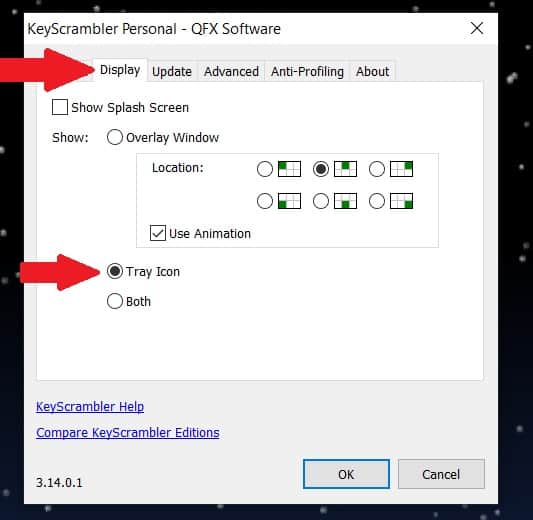
5. Choose the “Display” tab on the top, and customize your display options as you see here:
Congratulations, now all hackers will see if they try to snoop is gibberish!
Step 5, Bookmark all your important social and financial websites
You are clean!! I mean, your PC is clean. Now, let’s make sure it stays that way.
One of the most common ways hackers trick you into voluntarily handing over your username and password (especially for bank accounts) is through Phishing attacks.
What is a Phishing email attack?
Here is how Phishing works: Someone (could be a hacker, or your ex) sends you an official-looking email with a link to a fake website. This fake website is specifically designed to look exactly like your bank’s website (or Facebook, or…etc). The goal is to fool you into entering your username and password as you try to log in. Now the hacker has your username and password!
Luckily, these types of attacks are easy to avoid.
How to avoid and foil Phishing email attacks?
- Do not click on links sent to you by email, no matter how official they look
- Use your browser’s Bookmark bar to save all the essential social and financial sites that you use so you can safely visit them every time.
The instructions to show the bookmark bar for your browser are a bit different for each browser (such as Microsoft Edge, Google Chrome, Firefox…etc.) Choose your browser from the list below and follow the specific instructions.
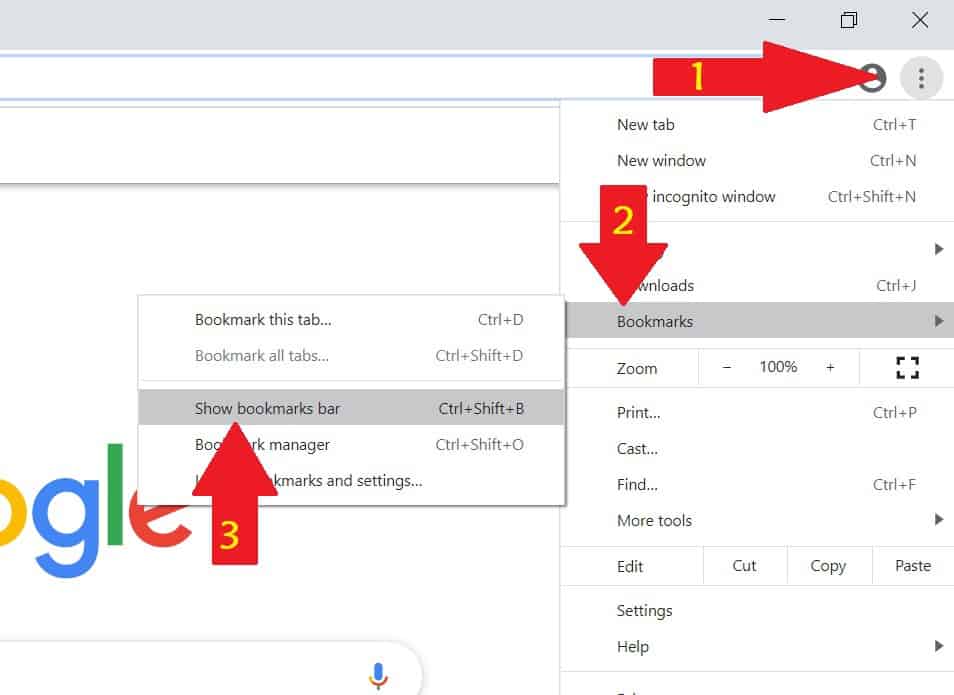
In Google Chrome,
- Open your browser and click the icon with three horizontal bars on the top right corner to open the control panel.
- Go to “Bookmarks” and choose “Show bookmarks bar.”
In Microsoft Edge,
- Click the icon with three horizontal bars in the top right corner to open the control panel.
- Go to “Favorites” and choose “Show favorites bar.”
Now, the most crucial step! Go to the official site for your bank (for example, search Google for CitiBank) then click on the official link. Once you are on the official site, highlight the address in the address bar, drag it, and drop it on the bookmark/favorites bar. Do the same for all your financial sites, then social media sites and email sites.
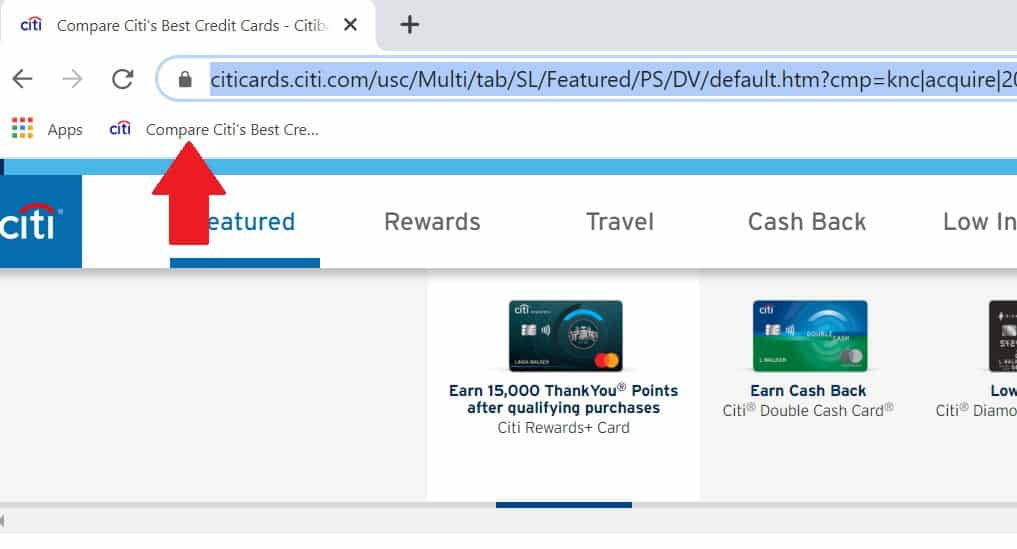
From this moment on, whenever you want to check your bank account balance, you only click the link in your bookmark bar! If you receive an email from your bank asking you to do something, do not click the link. Use your bookmark to go to the bank site.
Step 6, Use a password manager to generate unique random passwords
Do you have a long unique random password for each site you log into? If you are not sure what “a long unique random password” looks like, here is one: ati3Eg$*j&Wk3D(dc6
I just generated this password using Roboform, my password manager. This password is secure and impossible for anyone to guess. Of course, it is also impossible for me to remember. This is where a password manager comes very handy.
Why do you need long unique random passwords?
Because one the oldest (and still very effective) methods of hacking someone’s online account is guessing their password. If your ex already knows your Instagram password, he or she may try to use it (or a variation of it) on Facebook, or your bank!
What is a Brute Force attack?
Professional hackers program their computer to try thousands and thousands of different passwords on a specific site (common passwords, phrases, movie titles) until the computer finds the right one that works!
By using a password manager, you can add a huge layer of security to all your online accounts, make them virtually immune to brute force attacks, and safe from your obsessed ex.
I have used Roboform password manager for over a decade, and it is a wonderfully easy to use program. Here is a link to download Roboform. Roboform has a free version, but it is only good on one device (which is very impractical, trust me). I recommend that you opt for Roboform Everywhere and download it. Roboform Everywhere can be installed and synchronized between all your PCs, Tablets, and Smartphones making life much easier. I will walk you through installing and using it.
- After you go through the checkout process at Roboform, download the file
- The downloaded file will most likely appear on the bottom of your internet browser (otherwise, look for the Roboform Setup.exe file in the “downloads” folder on your computer.)
- Click the setup files to start the installation process
- Roboform is likely to ask you to close your browser and other applications. Make sure to come back to this SecureHomeHero page.
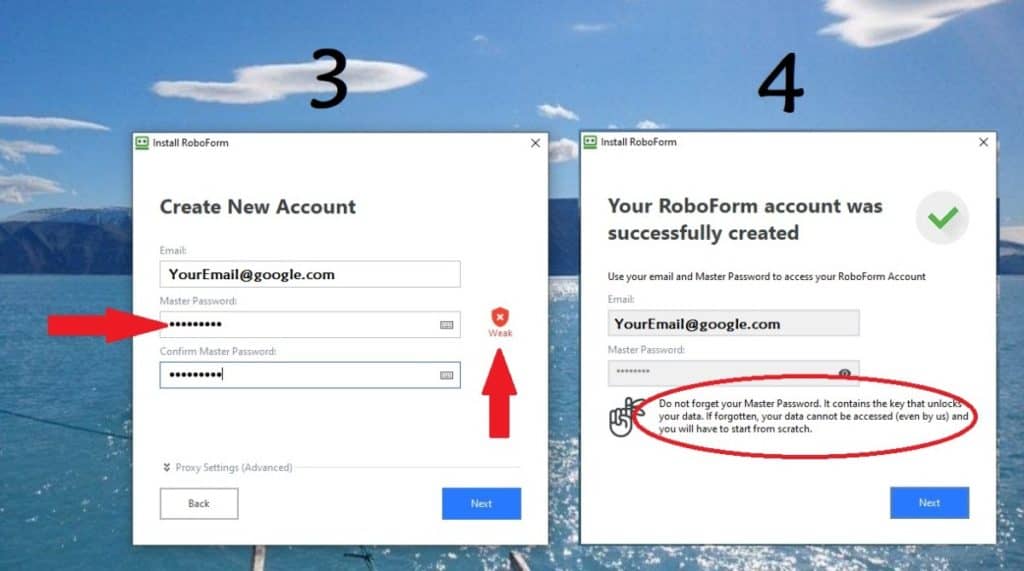
- When promoted enter your email address (this will be your username.)
- Important: choose your master password. This is the only password you will have to remember, so make it strong , more like a phrase with numbers, rather than a single word.
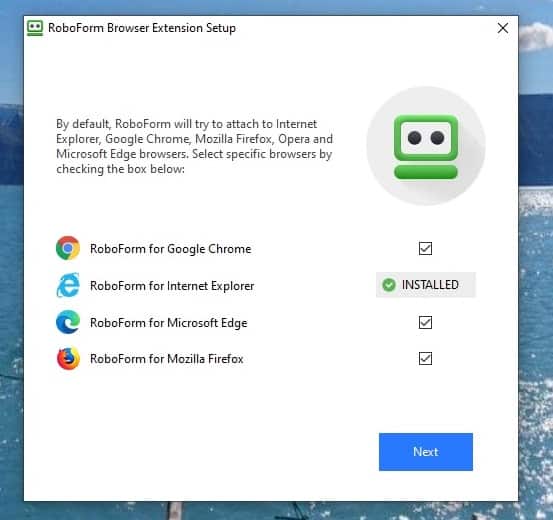
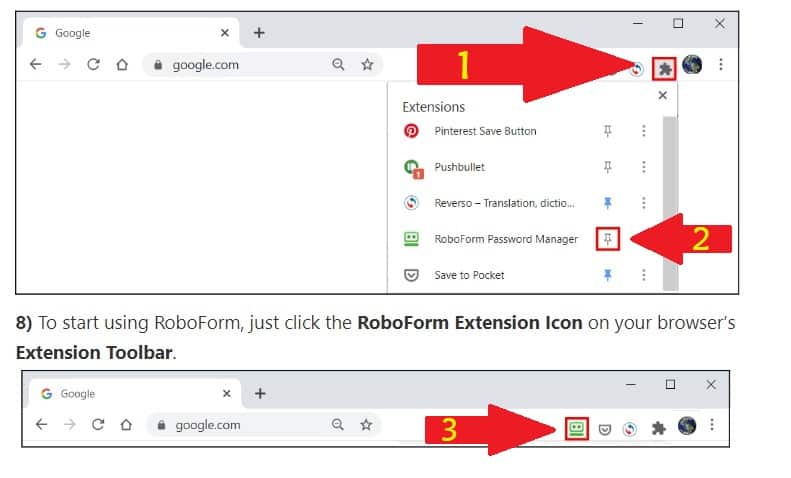
I have included a video below to help you start using this amazing program. It may feel awkward at the beginning, but trust me, soon you will wonder how you lived without it for so long.
Note: After you install Robooform, watch the video, and use the program, make sure t install the Roboform app on your smartphone and tablets.
Step 7, Keep your master password in a paper notebook!
Ok, so you just put time, effort, and a little bit of money into your Roboform password manager. You have generated long, unique random passwords for all your online accounts. Great job! But, it all hinges on your master password. If you forget your master password, you will lose access to all your accounts. I have personally experienced memory lapses and brain farts, so it could happen to you.
It is not safe is to save your master password on your computer because your computer may crash. Do not put it in your phone because your phone may get lost or stolen. The safest option is an old fashion one. Write your master password down on paper in a notebook, and secure the notebook in a safe, or in a bank’s safety deposit box.
Any notebook will do, but this might be a golden opportunity for you to get your life (and death) in order. Check out this “In Case of Emergency Workbook” on Amazon that has space specifically for passwords and so much more (like medical, history, emergency contacts, and such.)
Step 8, Install a full security suite program to monitor your computer for spyware, viruses, webcam and microphone access
You have invested about an hour of your time to clean, secure, and protect your computer, but your time is valuable, and you cannot do this every week. It is time to relax and let the professionals handle this task (and many more) for you.
There are many security programs out there. My favorite, by far, is NortonLifeLock because it comes loaded with top-notch features. Best of all, it runs silently in the background and only sends you notifications when necessary (like when your webcam or microphone are accessed!)
NortonLifeLock is an excellent antivirus, anti-ransomware, anti-phishing, and privacy protection suite (more on that later.)
While most of the programs I recommend are free, a security program at this level will cost you a little bit of money. Luckily, NortonLifeLock runs specials for new users (often as much as 30% off!). You can click here to check their current special offers. I would recommend you choose NortonLifeLock for up to five devices (you can protect your PC, smartphone, laptop, and such).
Step 9, Download and install a two-factor authentication (2FA) app on your smartphone.
Congratulations! You have made HUGE strides in securing your digital life. Let’s take one more step. It is all about peace of mind. More specifically, I want you to have peace of mind that even if a hacker (or your ex) gets a hold of one of your usernames and passwords, he or she will not be able to log into your account! Yes, this is possible if you use 2FA or two-factor authentication.
This step is optional; if you do not have a smartphone or do not want to set up 2FA, you can skip ahead to step 11.
What is 2FA or Two-Factor Authentication?
Two-factor authentication is an extra layer of security for logging into online accounts. After you enter your username and password, the site will ask for a 6-digit code randomly generated by an app on your phone. These codes change every 30 seconds, so even if someone has your password, they will not be able to login if they do not have access to your phone.
2FA will become much clearer in a few minutes. For now, please go to your phone and download an app called “Authy.”
- Open the “Authy” app and enter your phone number and email address.
- Verify your account with the registration code.
- Tap on the accounts icon (bottom of the screen)
- Turn “Authenticator Backups” on.
- Type in a long secure password for backups (for added security use a phrase rather than a word.)
- Tap Enable backups
- Important: Write the backups password in your paper notebook (this is critical in case you lose or upgrade your phone!)
Here is a video to walk you through the process,
Step 10, Activate 2FA security login for your online accounts.
Most banking, email, and social media accounts offer a 2FA security login option. Unfortunately, they do not advertise it or make it easy to find. To familiarize you with the process, I will walk you through how to active 2FA on your Gmail account (if you have one), and on your Roboform Password Manager.
For other accounts, especially banking, please Google to find the steps needed. For example, google the following “How do I activate 2FA on my PayPal account.”
Note: Whenever you are asked to use your “Google Authenticator” app, use your “Authy” app instead. They work the same, plus Authy has extra features.
Here are the steps for activating 2FA for Gmail,
- Log into your Gmail Account
- Click on the following link: https://myaccount.google.com/u/0/security?hl=en
- Under “Signing in to Google,” select 2-Step Verification and then Get started.
- Follow the on-screen steps.
- When you are asked to use your “Google Authenticator” app, use your “Authy” app instead. They work the same, (Authy has extra features)
- Once done, you should see a small icon in your Authy app that corresponds with this Google account.
From now on, when you (or someone else tries to) try to log into your Gmail from a new device, you will be asked to enter the six-digit number that appears in your Authy app in addition to your username and password.
Next, let’s activate 2FA for your Roboform account. This is an important step to guard your Roboform account even if someone gets a hold of your master password.
Here are the steps for activating 2FA for your RoboForm password manager,
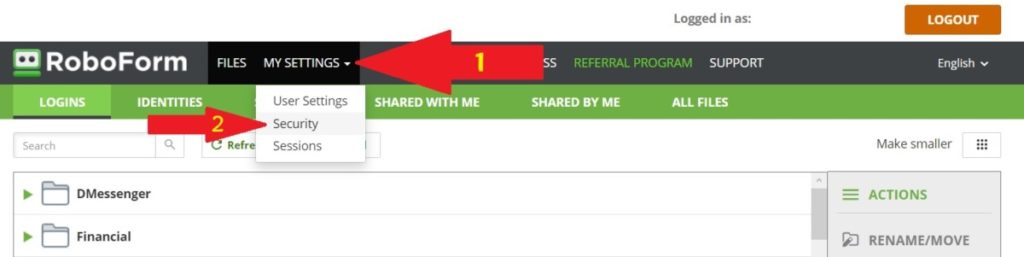
- Go to www.RoboForm.com and log into your RoboForm Online Account
- Under the “My Settings” menu in the upper navigation bar, choose “Security”
- Under “Send the One Time Password via Google Authenticator.”
- Scan the QR code or manually enter the secret key into your Authy app.
- Once you’ve scanned the QR code or entered the secret key, the Authy app will provide you with a six-digit number. (hurry, this number changes every 30 seconds)
- Enter the number into RoboForm where it says “Enter OTP from Google Authenticator App”
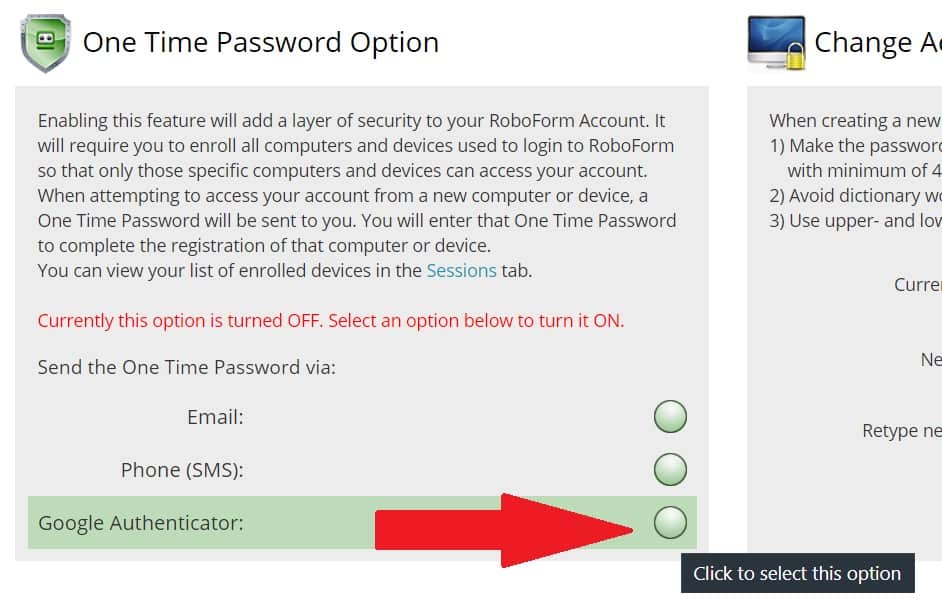
From now on, when you (or someone else tries to) use your RoboForm account from a new device, you will be asked to enter the six-digit number that appears in your Authy app in addition to your username and master password.
Step 11, When outside your home, use a VPN connection
Here is a piece of advice: do NOT trust any wifi network except the one at your house. Please do not trust the wifi network at the local coffee shop, at work, or the one at your best friend’s house because they may be compromised or monitored and can easily expose all your information.
Does this mean that I cannot use my laptop to access the internet outside my house?!
Of course, you can safely use your laptop wherever you like if you connect via a VPN or Virtual Private Network. Do not let the big words intimidate you. In short, a VPN encrypts and protects your data while it travels the internet. It is like putting your letter in a sealed envelope while you sent it through the mail. Here is the best part: Remember the NortonLifeLock suite you just installed in step 8? It has a free VPN feature built-in! Some VPN services limit your use to 200MB a day (good for checking email but not streaming music or movies). NortonLifeLock gives you unlimited data!
Here is how to use VPN on your NortonLifeLock,
When you are outside your home, and you want to connect to a public Wifi network, do the following:
- When you are using a wifi network outside your home, like a coffee shop wifi, for example, log into the coffee shop’s network
- From the bottom lower right of your screen, click the Norton VPN icon (yellow circle)
- A window will open, from the top menu, choose “Virtual Location”
- Wait for the connection to be established
- Now you are connected via VPN! Browse the internet and have fun
Note: Make sure to use VPN on your phone and tablet when outside the house.
Step 12, Congratulations!
When it comes to online security, you are light-years ahead of 99% of the people. You deserve a big congratulations and a huge round of applause!
There is one thing left: common sense., because you can seriously undermine your hard work if you are careless.
- Do not share your master passwords with anyone you do not trust 100% (love does not always equal trust!)
- Do not be careless with your paper notebook
- Do not click on email links and open unknown email attachments.
- Always use your best judgment on and off line
Congratulations my friend, I certify you a Digital SecureHomeHero!
Did I miss anything? Did any of the steps above not work for you? Please let me know.
As a new Digital SecureHomeHero, here are a few other blogs you may enjoy:
How to Keep Your WiFi Internet Even Connection During Power Outage

